The MCNC web security solution can be used by an LEA or charter school to replace or complement their existing content filtering solution. When SSL inspection is used, a Root Certificate signed by Zscaler needs to be installed in each browser to prevent certificate error messages. Gartner Group is promoting the acronym CASB cloud access security broker to describe this category of functionality. For example, authentication can be disabled for the guest wireless network, while leaving it enabled for all other networks. All common browsers are supported on Windows, Mac and Linux platforms, regardless of the location of the user. This article contains content that is written like an advertisement. ![]()
| Uploader: | Arall |
| Date Added: | 7 July 2014 |
| File Size: | 70.97 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 98539 |
| Price: | Free* [*Free Regsitration Required] |
Security patches should be kept up to date and other best ezagnet for system security should be followed. For example, it tests to see whether virus samples hosted on zscaleg delivery networks are blocked, it attempts to exfiltrate valid payment card and social security numbers, and it detects whether communications with servers in prohibited countries such as North Korea and Iran are blocked.
Traffic Redirection Once the policy rules have been configured, traffic eaagent be redirected to the enforcement nodes. Site-wide policy applies to everyone, user unknown. Defined Categories of Service Users can be added manually or imported from a file. User and group level filtering and audit trail. Zscaler Mobile Security extends its real-time analysis and protection to mobile devices in BYOD environments by routing mobile traffic through its global cloud.
Zscaler requires no on-premises and on-device hardware or software. Related manuals datasheet zscaler email security. Drill down reports provide a means to quickly understand user activity, categories zscxler web sites visited, traffic volume and filtering policy compliance. Worldwide Web Security Support for content-filtering of remote and mobile users is available for most mobile devices through use of PAC files.
Zscaler will then check the validity of the cert and then create a new cert signed by Zscaler.
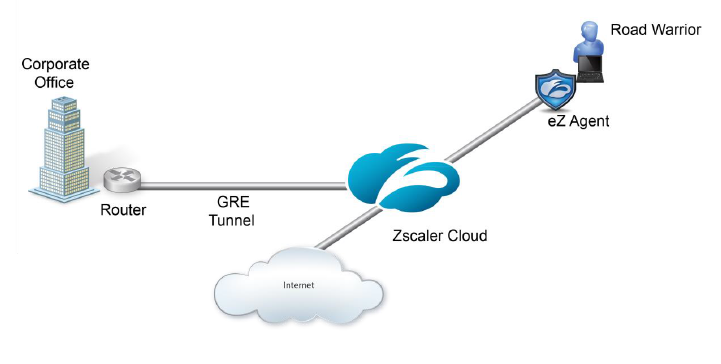
Policy is not applied to SSL traffic from remote and mobile users unless it is decrypted and inspected. However PAC files have limitations, e.
Zscaler is designed ezagentt address the challenge of managing security in a world where cloud computing, mobility and the Internet of things are eroding the network perimeter. Rules can be applied to existing and custom content categories.
Do you need a help? Even if security was the main driver for this project, ECS today profits from more benefits as the Security Platform help to solve network bandwidth issues. Web traffic is analyzed to detect P2P applications, traffic anonymizers, and bot-net command and control traffic.
WHOIS | Zscaler Inc. | AbuseIPDB
For environments with shared devices, users can be required to re-authenticate after each browser session or after more than a day of inactivity. From Wikipedia, the free encyclopedia. Securing the Environment The effectiveness of the content filtering capability relies on sound practices in system and network security.
Network securitycomputer securityInternet security. LEAs or charter schools that plan to deploy these devices will need to consider device security measures in order to prevent fzagent from changing the settings required to enforce filtering policy.
No filtering policy, user unknown. When a policy rule is matched, the connection can be blocked, accepted, monitored or fzagent the user with a warning message.
Encrypted transaction blocking is only available for on-net users. A LEA or charter school that wishes to keep their existing content filtering solution can still take advantage of the security protection features to provide an additional layer of security around their network perimeter. For this reason, the blocking policy for encrypted traffic applies to all users. POSTlocation, and time of day.
K12 Services - Web Security
As the incumbent solution did not support SSL inspection, it also failed to deliver full protection against modern malware. The new cert will be sent to the Web Browser, and assuming that the user has pre-installed a company root cert, the browser will check the validity of the cert and then accept and install the cert and then will continue to access the website.
Laptops and workstations should be restricted so that end users cannot modify proxy settings or download tools that may be able to circumvent content filters.

Комментариев нет:
Отправить комментарий